In today’s digital age, the importance of cybersecurity cannot be overstated. Additionally, with an ever-increasing number of cyber threats and attacks, it is crucial to understand how to find vulnerabilities in systems and networks. Therefore, this comprehensive guide will take you through the process of identifying vulnerabilities and ensuring the security of your digital assets.
Understanding Vulnerabilities
1. What Are Vulnerabilities?
In the realm of cybersecurity, vulnerabilities are weaknesses or flaws in software, hardware, or network systems that can be exploited by malicious actors. These vulnerabilities can be unintentional, resulting from coding errors, or intentional, such as backdoors for system administrators.
2. Why Are Vulnerabilities a Concern?
Vulnerabilities pose a significant concern because they can lead to security breaches and data compromises. When exploited, vulnerabilities can have severe consequences, including data theft, system manipulation, and financial losses.
One of the most notorious examples of vulnerabilities leading to a security breach is the Equifax data breach in 2017. Consequently, Equifax, one of the largest credit reporting agencies in the United States, suffered a breach that exposed the personal information of 147 million people. Specifically, the breach was the result of an unpatched vulnerability in the Apache Struts web application framework.
3. Who Looks for Vulnerabilities?
Various entities are interested in identifying vulnerabilities, each with their motivations and methods. These include:
- Ethical Hackers: Ethical hackers, also known as white-hat hackers, actively search for vulnerabilities in systems, networks, and applications to help organizations patch these weaknesses before malicious hackers can exploit them.
- Security Researchers: Security researchers often work independently or for security firms, conducting in-depth analyses of software and systems to uncover vulnerabilities.
- Malicious Hackers: Unfortunately, not all individuals who search for vulnerabilities have good intentions. Moreover, malicious hackers seek to exploit vulnerabilities for personal gain, often causing harm to individuals and organizations.
Preliminary Steps
4. Setting Clear Objectives
Before you start searching for vulnerabilities, it’s essential to define clear objectives for your assessment. What are you trying to achieve? Are you focusing on a specific system, network, or application? Setting clear goals helps streamline your efforts.
5. Gathering Information
Gathering information about the target system or network is a crucial step in the vulnerability assessment process. In particular, this information can include details about the architecture, network topology, and software versions in use. To facilitate this data collection, tools like Shodan, Censys, and Nmap can be immensely helpful.
Scanning for Vulnerabilities
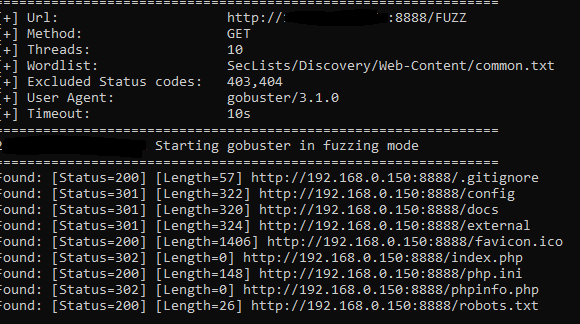
6. Port Scanning
Port scanning is the process of checking for open ports on a system, which can serve as potential entry points for attackers. Moreover, common tools utilized for port scanning include Nmap, Netcat, and Wireshark.
Port scanning is a critical step in assessing the security posture of a system or network. Furthermore, by identifying open ports, attackers can determine potential avenues for unauthorized access or exploitation.
Additionally, Nmap, one of the most widely used port scanning tools, offers a variety of scanning techniques to comprehensively map out network services and their associated vulnerabilities.
Netcat, another versatile tool, provides additional functionalities beyond port scanning, such as establishing network connections and transferring data.
Wireshark, on the other hand, offers packet sniffing capabilities, allowing users to capture and analyze network traffic, which can reveal valuable insights into potential security weaknesses.
Together, these tools play a vital role in helping security professionals identify and address vulnerabilities before they can be exploited by malicious actors.
7. Vulnerability Scanners
Vulnerability scanners are specialized tools designed to automate the process of identifying vulnerabilities. Additionally, they often come with extensive databases of known vulnerabilities and can efficiently scan systems for weaknesses.
When choosing a vulnerability scanner, consider factors such as the scope of the assessment, ease of use, and the frequency of updates to the vulnerability database.
8. Network Mapping
Network mapping involves creating a visual representation of the target network’s structure. Consequently, this helps identify potential vulnerabilities and their associated systems. Tools like Zenmap and OpenVAS can aid in network mapping.
Furthermore, by accurately depicting the network topology, administrators can gain insights into the layout of devices, connections, and potential entry points for attackers. This information is invaluable for devising robust security strategies and implementing necessary safeguards to protect against cyber threats.
Analyzing Vulnerabilities
9. Identifying Open Ports
Open ports can be potential vulnerabilities, as they may provide access points for attackers. Consequently, identifying these open ports is a critical step in vulnerability assessment. Common tools for port identification include Nmap and PortQry.
10. Enumerating Services
Service enumeration involves discovering the services running on a system. This can provide insights into potential vulnerabilities related to specific services. Notably, enumeration tools such as Enum4linux and SNMP Walk are commonly employed for this purpose.
11. Assessing Patch Levels
Understanding the patch status of software
and systems is a vital aspect of vulnerability assessment. Outdated or unpatched software often contains known vulnerabilities that can be exploited by attackers. To assess patch levels:
- Check for Software Updates: Ensure that all software and systems are up to date with the latest security patches. Regularly updating software is a fundamental security measure.
- Utilize Vulnerability Databases: Explore vulnerability databases like the Common Vulnerabilities and Exposures (CVE) system to check if any known vulnerabilities exist for the software or systems in use.
- Patch Management: Implement a robust patch management process to promptly address any identified vulnerabilities. This involves planning, testing, and deploying patches across the organization.
12. Vulnerability Databases
Vulnerability databases are invaluable resources for security professionals. They provide detailed information about known vulnerabilities, including their severity, affected systems, and available patches. Some prominent vulnerability databases include:
- National Vulnerability Database (NVD): Maintained by the National Institute of Standards and Technology (NIST), NVD is a comprehensive source of vulnerability information.
- Common Vulnerabilities and Exposures (CVE): CVE is a standardized list of common identifiers for publicly known cybersecurity vulnerabilities.
- Exploit Database: This database contains a wide range of exploits, including proof-of-concept code, providing insights into how vulnerabilities can be exploited.
Exploiting Vulnerabilities
13. Ethical Hacking
Ethical hacking is the practice of intentionally probing and exploiting vulnerabilities in systems, networks, and applications for legitimate purposes. This hackers, also known as white-hat hackers, have a crucial role in helping organizations strengthen their security measures. Key principles of ethical hacking include:
- Authorization: Ethical hackers must obtain proper authorization before testing systems.
- Responsible Disclosure: If ethical hackers discover vulnerabilities, they should follow responsible disclosure practices, alerting the organization to the issue and providing time to remediate it.
14. Common Exploitation Techniques
Understanding exploitation techniques is essential for both ethical hackers and security professionals to test and secure systems effectively. Some common exploitation techniques include:
- Buffer Overflow: Exploiting software vulnerabilities to manipulate or overrun the memory buffer of a system.
- SQL Injection: Injecting malicious SQL queries into a vulnerable application to access or manipulate the database.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web pages viewed by other users, potentially compromising their data or accounts.
- Social Engineering: Manipulating individuals to disclose confidential information or perform actions that may compromise security.
Reporting and Documentation
15. The Importance of Reporting
Once vulnerabilities are identified, it is essential to report them promptly. Reporting vulnerabilities is crucial for several reasons:
- Mitigation: Reporting vulnerabilities allows organizations to take action and mitigate potential risks.
- Ethical Responsibility: Ethical hackers and security researchers have an ethical duty to report vulnerabilities responsibly, helping protect the digital landscape.
16. Creating Vulnerability Reports
When creating vulnerability reports, ensure they are clear, comprehensive, and actionable. A well-structured report typically includes:
- Description of the Vulnerability: Detail the nature of the vulnerability, including how it can be exploited.
- Severity Assessment: Assess the severity of the vulnerability based on its potential impact.
- Steps to Reproduce: Provide a step-by-step guide on how to reproduce the vulnerability.
- Recommended Mitigation: Suggest ways to mitigate or fix the vulnerability.
Mitigating Vulnerabilities
17. How to Address Vulnerabilities
Mitigating vulnerabilities is a critical step in the cybersecurity process. After vulnerabilities are identified, organizations should take the following steps to address them:
- Prioritization: Assess the severity of each vulnerability and prioritize based on potential impact.
- Patch Management: Implement a structured patch management process to apply updates and fixes promptly.
- Security Policies: Develop and enforce security policies and practices to reduce the likelihood of vulnerabilities in the future.
18. Patch Management
A robust patch management process is essential for addressing vulnerabilities efficiently. Transitioning to the key components of effective patch management, they include:
- Vulnerability Identification: Regularly scanning systems and networks to identify vulnerabilities and assess their severity.
- Patch Prioritization: Prioritizing patches based on the criticality of vulnerabilities, potential impact on business operations, and the availability of exploits.
- Patch Testing: Testing patches in a controlled environment to ensure compatibility with existing systems and applications and to minimize the risk of unintended consequences.
- Patch Deployment: Deploying patches in a timely manner to mitigate identified vulnerabilities and reduce the window of opportunity for exploitation by attackers.
- Monitoring and Verification: Monitoring systems post-patch deployment to verify that patches have been successfully applied and to detect any issues or anomalies that may arise.
- Documentation and Reporting: Maintaining detailed records of patching activities, including the applied patches, deployment dates, and any associated issues encountered, to ensure accountability and facilitate compliance with regulatory requirements.
By implementing these key components, organizations can establish a proactive approach to patch management that enhances their ability to protect against emerging threats and safeguard sensitive data and critical assets.
Ongoing Vulnerability Assessment
19. Continuous Monitoring
Vulnerabilities can emerge at any time, so continuous monitoring is crucial. This involves:
- Regular Scanning: Continuously scanning systems for vulnerabilities and weaknesses.
- Intrusion Detection: Employing intrusion detection systems to alert you to suspicious activities.
- Security Information and Event Management (SIEM): Using SIEM tools to collect and analyze security data from various sources.
20. Staying Informed
Staying informed about the ever-evolving landscape of cybersecurity is essential. Here are some ways to keep up with the latest security threats and vulnerabilities:
- Security Blogs and News: Regularly read cybersecurity blogs and news sources to stay updated on emerging threats and vulnerabilities.
- Participate in Forums: Engage in cybersecurity forums and communities to learn from experts and share your knowledge.
- Continuous Learning: Invest in ongoing education and training to remain current in the field.
Conclusion
The ability to find vulnerabilities and secure digital assets is a fundamental skill in today’s world. Whether you’re an ethical hacker, a security professional, or an individual concerned about personal cybersecurity, understanding how to find vulnerabilities is critical to staying safe in the digital realm.
Remember that cybersecurity is an ongoing process, and the threat landscape is constantly evolving. By following best practices and staying informed, you can better protect your systems and networks from potential threats