Websites are complex systems made up of directories, folders, and pages that contain specific instructions and data for various tasks and requests. Interacting with a website often involves navigating through a series of directories, some of which may not be visible to the general public. However, hackers may discover these hidden directories and leverage them for their own purposes. How do they go about identifying and exploiting these hidden directories?
What is Directory Bursting?
Directory bursting, also known as path enumeration, is a method used by attackers to discover hidden or restricted directories on a website or web application. It involves systematically testing different directory and file names within a website’s directory structure to uncover any hidden or restricted directories that may contain sensitive information.
Attackers may use automated tools to launch a brute-force attack, trying various directory and file names in a rapid sequence until a valid directory or file is found. Alternatively, attackers may use manual techniques to identify hidden directories by studying the website’s source code or by guessing the names of directories based on common naming conventions.
Once a hidden directory is discovered, attackers can potentially gain access to sensitive data, such as confidential files or user data, or exploit vulnerabilities within the directory to launch further attacks. To prevent directory bursting attacks, website administrators can implement security measures such as access controls, user authentication, and directory indexing restrictions.
What is a Directory?
In computing, a directory is a file system structure that stores and organizes files, other directories, and metadata such as file permissions and file attributes. It is also known as a folder in some operating systems.
A directory can contain files, subdirectories, and links to other directories. It provides a way to organize and manage files on a computer or network, allowing users to easily navigate through a hierarchy of files and directories.
Directories are typically organized in a tree-like structure, with a root directory at the top and subdirectories branching off from it. The directory path specifies the location of a file or directory within the directory tree.
Directories can have different levels of permissions, allowing users or groups to read, write, or execute files within them. Directories can also have attributes that specify their properties, such as whether they are hidden or system directories.
In web development, directories are used to organize files and resources on a website or web application. Web directories can be accessed by users through URLs, and can be used to store web pages, scripts, images, and other website content.
How Does Directory Bursting Work?
Attackers use automated tools or manual techniques to test various directory and file names within a website’s directory structure. They typically start with common directory names and then move on to less common or obscure names until a valid directory is found.
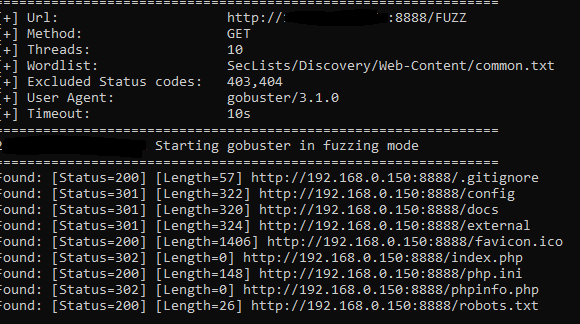
The process of directory bursting involves sending a large number of HTTP requests to the target website with different directory and file names. The attacker may use a tool such as DirBuster, Dirbuster-ng, or WFuzz, which automate the process by sending multiple HTTP requests with different directory names in a short period of time.
If the website returns a “404 Not Found” error code, the attacker knows that the directory or file does not exist. However, if the website returns a “200 OK” code, the attacker knows that the directory or file exists and can potentially be accessed.
Once a hidden directory is discovered, the attacker can use it to access sensitive data, such as confidential files or user data, or to exploit vulnerabilities within the directory to launch further attacks.
Directory Bursting Tools and Wordlists
Directory bursting tools typically work by systematically trying different combinations of directory and file names, based on a set of predefined wordlists. These wordlists contain commonly used or easily guessable names for directories and files, such as “admin”, “backup”, “config”, “login”, “phpmyadmin”, “robots.txt”, and so on.
Examples of directory bursting tools include DirBuster, DirSearch, Gobuster, and WFuzz. These tools can be used to automate the process of enumerating directories and files on a web server, and can be configured to use different wordlists, custom extensions, and other parameters to increase the chances of discovering hidden or sensitive content.
Wordlists, on the other hand, are simply lists of words, phrases, or symbols that are commonly used or known to be associated with a particular domain, topic, or language. In the context of directory bursting, wordlists are used to generate a large number of potential directory and file names that can be tried against a web server.
Wordlists can be created manually, by compiling a list of relevant words and phrases, or they can be downloaded from online repositories or generated using automated tools. Some popular wordlists for directory bursting include the SecLists Project, Rockyou.txt, FuzzDB, and Dirbuster-wordlists.
Protect Your Website From Directory Bursting
To protect your website from directory bursting, here are some tips:
- Use a strong password: Directory bursting often involves trying different combinations of usernames and passwords to gain access to sensitive directories and files. Using a strong password that is difficult to guess can help prevent unauthorized access.
- Implement rate limiting: You can limit the number of requests that can be made to your website from a single IP address within a certain period of time. This can help prevent directory bursting attacks by slowing down or stopping automated tools from systematically trying different directory and file names.
- Disable directory listing: Directory listing allows anyone to view the contents of a directory on a web server. Disabling directory listing can help prevent attackers from enumerating the directories and files on your website.
- Use secure coding practices: Writing secure code can help prevent directory bursting attacks by minimizing the number of vulnerabilities that can be exploited. This includes properly validating user input, sanitizing data, and using secure authentication mechanisms.
- Monitor server logs: Regularly monitoring your server logs can help detect and prevent directory bursting attacks by identifying unusual or suspicious activity, such as multiple requests for non-existent files or directories.
- Use web application firewalls: Web application firewalls (WAFs) can help protect your website from directory bursting attacks by filtering incoming traffic and blocking malicious requests.
Conclusion –
Protecting your website from directory bursting requires a combination of technical and non-technical measures, including implementing secure coding practices, using strong passwords, and monitoring server logs. By taking proactive steps to secure your website, you can reduce the risk of directory bursting attacks and improve the overall security of your online presence.